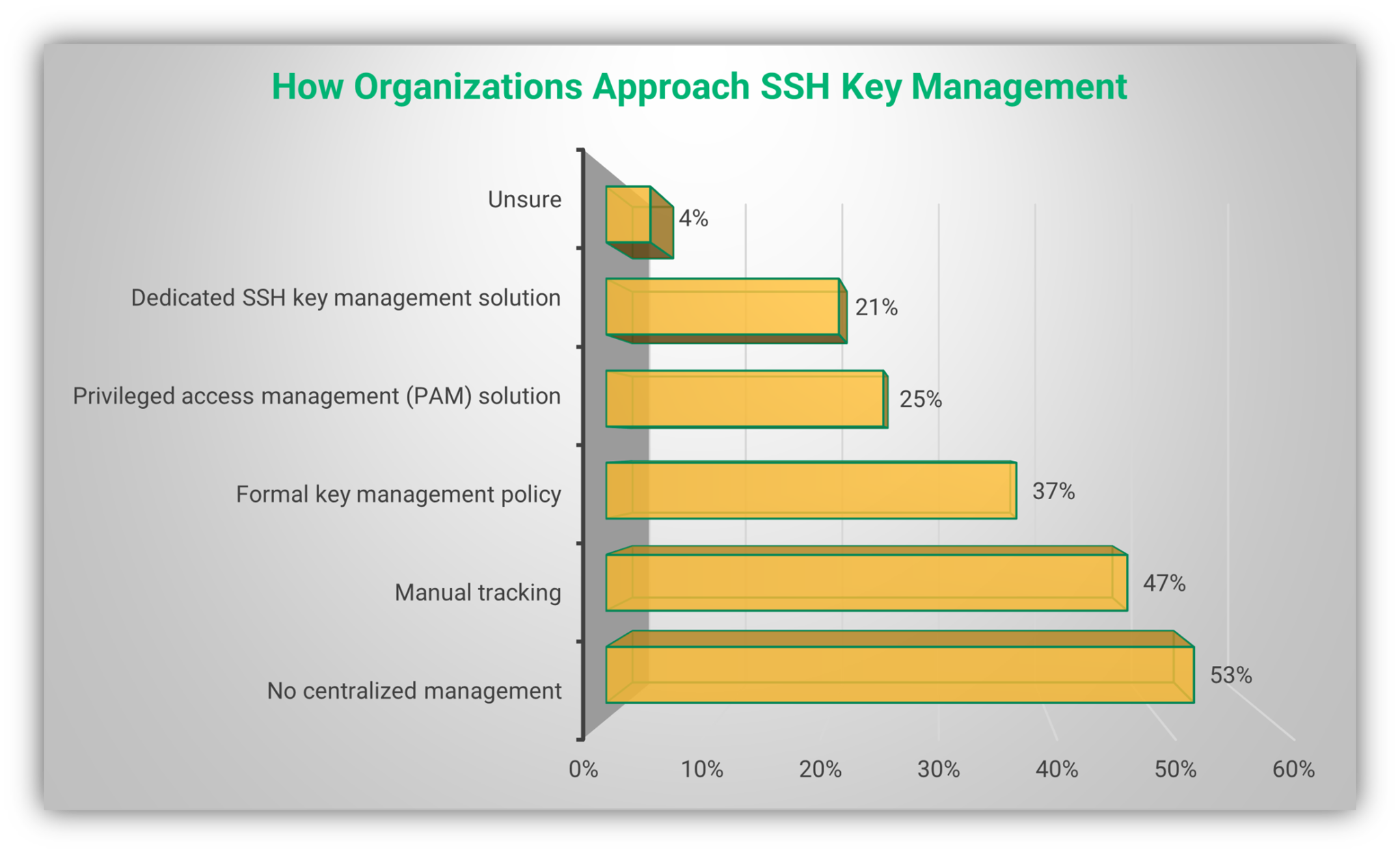
Managing SSH keys in the era of remote IoT operations has become more critical than ever. With the rise of connected devices and distributed systems, ensuring secure access while maintaining efficiency is no longer optional—it's essential. Best RemoteIoT SSH key management practices provide the foundation for safeguarding your infrastructure against unauthorized access and potential breaches. Whether you're managing a small fleet of devices or overseeing an enterprise-level IoT network, mastering SSH key management is key to success.
Imagine this: you're running a remote IoT setup with hundreds of devices scattered across multiple locations. How do you ensure that only authorized users can access these systems? That's where SSH keys come into play. They act as digital keys to unlock secure connections, but managing them properly is a challenge. This article dives deep into the best practices for remote IoT SSH key management, offering actionable tips and expert insights to help you stay ahead of the curve.
From understanding the basics of SSH keys to implementing advanced strategies for securing your IoT infrastructure, we'll cover it all. So, buckle up and let's explore how to make your remote IoT operations not just secure, but rock-solid!
- Discover The Mystical Power Of The 1965 Chinese Zodiac Your Ultimate Guide
- Robert Pattinson And Harry Potter The Untold Story Of A Stars Journey
Table of Contents
- Introduction to RemoteIoT SSH Key Management
- Understanding SSH Keys
- Why SSH Key Management Matters
- Best Practices for RemoteIoT SSH Key Management
- Top Tools for SSH Key Management
- Securing Your SSH Keys
- Common Challenges in SSH Key Management
- Automation in SSH Key Management
- The Future of RemoteIoT SSH Key Management
- Conclusion and Next Steps
Introduction to RemoteIoT SSH Key Management
So, what exactly is RemoteIoT SSH key management? In simple terms, it's the process of organizing, securing, and maintaining SSH keys used for authenticating remote connections to IoT devices. These keys are like digital passports that allow devices and users to communicate securely over the internet. But here's the catch—just having SSH keys isn't enough. You need to manage them properly to avoid security risks.
Think about it—what happens if an SSH key falls into the wrong hands? Hackers could gain unauthorized access to your devices, leading to data breaches, system downtime, or even financial losses. That's why understanding and implementing best practices for SSH key management is crucial for anyone working with remote IoT setups.
Understanding SSH Keys
Before we dive into the nitty-gritty of managing SSH keys, let's break down what they are and how they work. SSH keys are cryptographic keys used for authentication in Secure Shell (SSH) protocols. They come in pairs: a public key and a private key. The public key is shared with the devices you want to connect to, while the private key remains securely stored on your system.
- Doodle Garden Gnomes The Quirky Adorable Addition To Your Backyard
- How Long Can Saiyans Live Unlocking The Secrets Of Saiyan Longevity
Here's a quick rundown of how SSH keys work:
- The server stores the public key.
- The client uses the private key to authenticate itself to the server.
- If the keys match, the connection is established.
It's like a handshake, but with a lot more security!
Why SSH Key Management Matters
Now that we know what SSH keys are, let's talk about why managing them properly is so important. In today's interconnected world, the number of IoT devices is exploding, and so is the potential for security threats. According to a recent report, the global IoT market is expected to grow to over 25 billion devices by 2030. That's a lot of devices to manage—and a lot of potential entry points for attackers.
Here are a few reasons why SSH key management matters:
- Security: Proper SSH key management helps prevent unauthorized access and reduces the risk of breaches.
- Efficiency: Well-managed SSH keys streamline remote access processes, saving time and resources.
- Compliance: Many industries have strict regulations regarding data security, and proper SSH key management is often a requirement.
Best Practices for RemoteIoT SSH Key Management
Alright, let's get down to business. Here are some best practices for managing SSH keys in a remote IoT environment:
1. Use Strong Key Pairs
Weak keys are like unlocked doors for hackers. Always use strong key pairs with sufficient bit lengths. RSA keys with 2048 bits or ECC keys with 256 bits are good choices. And don't forget to protect your private keys with passphrases for an extra layer of security.
2. Rotate Keys Regularly
Just like you change your locks when you move into a new house, you should rotate your SSH keys periodically. This ensures that even if a key is compromised, the damage is limited.
3. Limit Key Usage
Don't give everyone access to everything. Use role-based access control (RBAC) to limit which keys can access specific devices or systems. This minimizes the attack surface and makes it easier to track who has access to what.
Top Tools for SSH Key Management
Managing SSH keys manually can be a nightmare, especially when dealing with large-scale IoT deployments. Thankfully, there are tools designed to make the process easier and more secure. Here are a few top contenders:
- HashiCorp Vault: A powerful tool for managing secrets, including SSH keys. It offers features like key rotation and access control.
- SSH Key Management System (SKMS): A dedicated solution for managing SSH keys across large networks.
- Ansible: An automation tool that can help with SSH key deployment and management.
Securing Your SSH Keys
Having strong SSH keys is great, but if they're not stored securely, it's all for nothing. Here are some tips for keeping your keys safe:
- Store private keys in secure locations, such as hardware security modules (HSMs) or encrypted drives.
- Use multi-factor authentication (MFA) for added security.
- Regularly audit your key inventory to ensure no unauthorized keys are in use.
Common Challenges in SSH Key Management
Even with the best tools and practices, managing SSH keys in a remote IoT environment can be challenging. Here are some common issues you might face:
- Key sprawl: As your IoT fleet grows, so does the number of keys. Keeping track of them all can be overwhelming.
- Outdated keys: Keys that aren't rotated regularly can become security risks.
- Lack of visibility: Without proper tools, it can be difficult to see who has access to what devices.
Automation in SSH Key Management
Automation is the key to overcoming many of the challenges in SSH key management. By automating tasks like key generation, rotation, and revocation, you can save time and reduce the risk of human error. Many of the tools mentioned earlier offer automation features, so it's worth exploring them to find the right fit for your needs.
The Future of RemoteIoT SSH Key Management
As technology continues to evolve, so will the methods for managing SSH keys. We can expect to see advancements in areas like:
- Quantum-resistant cryptography: As quantum computing becomes more prevalent, new encryption methods will be needed to protect SSH keys.
- AI-driven automation: Artificial intelligence could play a bigger role in automating and optimizing SSH key management processes.
- Blockchain-based solutions: Some experts believe blockchain technology could be used to create more secure and transparent SSH key management systems.
Conclusion and Next Steps
Managing SSH keys in a remote IoT environment is no small task, but with the right strategies and tools, it's definitely achievable. By following best practices, leveraging automation, and staying informed about the latest advancements, you can ensure your IoT operations remain secure and efficient.
So, what's next? Start by auditing your current SSH key management processes and identifying areas for improvement. Then, explore the tools and techniques discussed in this article to find the ones that work best for your setup. And don't forget to keep learning—security is an ever-evolving field, and staying ahead of the curve is key to success.
Got any questions or thoughts? Drop a comment below or share this article with your network. Together, let's make remote IoT SSH key management a breeze!
- Michael Bivins Net Worth A Deep Dive Into The Financial Empire Of A Music Legend
- 1996 Was The Year Of The Revolution A Time To Remember